There are several ways to deploy applications to users or devices that are managed by Microsoft Intune. In addition to application types, you must also take into consideration the method of assignment and how it will affect you long term from a management and maintenance standpoint.
Deploying an application installer via Intune is usually accomplished via a line of business (LOB) app or a Win32 app. If the application installer is packaged as a .msi file, it can typically be deployed within Intune natively as an LOB app. However, if the application installer is packaged as a .exe file or via some other method, some additional work is required and the app would then be deployed as a Win32 application.
Partner with Microsoft experts you can trust
If it’s time to take that first step toward leveling up your organization’s security, get in touch with Ravenswood to start the conversation.

The application assignment has two types as well: required or available. This seems straightforward, right? If a group of users or devices needs an application, deploy it as required; if it’s optional, make it available. The problem arises when you need to upgrade the application. With a required assignment, technically you could upload the new packaged application and tweak the detection rules. However, doing so with an available assignment won’t actually upgrade anything. The way around this is to utilize a feature called supersedence.
Win32 app supersedence is a newer feature that allows either a new version of an application or a completely different application to be made available or installed on an end user’s computer, replacing the previous version. The supersedence feature is well documented at Microsoft.
Using the Win32 app supersedence feature is quite simple, although some additional steps are required. Any Win32 app deployment, regardless of its assignment type, can use supersedence—and should use it, despite the additional steps.
Here’s how to use Win32 supersedence to deploy apps.
- Create and populate a security group containing users or devices that have installed the application.
Create a security group that is populated with all of the user or device objects that have the application currently installed. In a small environment, determining who has the application installed can be accomplished with little effort by opening the application within Endpoint Manager and looking at either the user or device install status. In larger environments or if upgrades are done often, a programmatic approach is recommended and is covered in Manage Entra (formerly Azure AD) Groups with the Graph API.
- Create the new Intune application configured with the supersedence feature.
Create a new Win32 application, duplicating the original in all configuration details but with three critical differences:
- Detection rules – The updated version of the application will likely have a newer file version than the previous, so you’ll need to update the method to detect that it has been installed and is the appropriate version.
- Supersedence – This feature has two options, to uninstall the previous version or not.
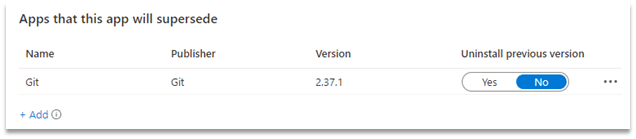
For most applications, you can select No, which will let the application manage the upgrade internally. However, if you’re working with an application that will install additional versions without removing the original, you should select Yes to trigger the older application’s uninstall command first before installation.
One additional benefit of selecting Yes is if you’re replacing one application with an entirely different application. An example of this would be removing one vendor’s VPN client because you are migrating to a different vendor that has its own VPN client.
- Assignment – Target the assignment to a test security group containing a single user or device first to do some basic testing to validate that the changes work for the new application.
Once the application installation has been validated successfully, remove the test security group assignment. Next, assign the previously created security group (containing production users or devices) as Required. Then assign any user or device as Available as normal, replicating the original assignments. Any user or device targeted will no longer see the old application within Company Portal, because it has been superseded by this new/replaced version.
- Monitor the upgrade process and clean up.
As workstations check in to Intune and the installations are processed, review both the old and new applications. You’ll see the installed user or device list shift from the old to the new list. Once the old application shows no user or device installs remaining, the upgrade is complete. The cleanup process is quite simple:
- Remove the supersedence link (configured in the new application).
- Remove the assigned security group configured in the new application from being required.
- Delete the old application from Intune entirely since it’s no longer needed.
- Delete the security group (optional).
Managing Win32 applications can be a complicated process compared to other application types. The experts at Ravenswood are eager to assist with any issues you may encounter. Contact our team to see how we can help with your project.












