Today, we’ll explore the signs of a pass-the-hash (PtH) attack and discuss methods to detect and prevent such attacks in your environment. At Ravenswood Technology Group, LLC, we have decades of expertise in securing and hardening Active Directory Domain Services environments.

In this article, I’ll share some key insights. If you need advice for your environment, feel free to comment or reach out on our website.
What is a Pass-the-Hash Attack?
Partner with Microsoft experts you can trust
If it’s time to take that first step toward leveling up your organization’s security, get in touch with Ravenswood to start the conversation.
A pass-the-hash (PtH) attack is a technique where a bad actor steals a user’s password hash from memory or storage and uses it to authenticate as the victim without needing to know their plaintext password. Authentication systems generate and store hashes of passwords instead of storing the actual passwords. During an authentication request, the entered password is hashed and compared with the stored hash; if they match, the user is authenticated. This type of attack, known as Lateral Movement, allows access to other systems on the network. It is most common in Windows systems when using NTLM authentication (more on this later). In this type of attack the stolen hash is used to authenticate to other systems the user has access to, and then more hashes can be harvested which expose even more users and systems. Once a system with privileged hashes is compromised, then the attacker has gained privileged access to the environment all without ever knowing a single password.
Kerberos authentication is not as susceptible to PtH, although Kerberos has its own security concerns. For example, an attacker with a stolen password hash could use a technique called “Overpass-the-hash” to request and receive a valid Kerberos ticket which would allow for a Pass-the-ticket attack. For a deeper dive into Kerberos and some of its unique security considerations, take a look at his article, Protecting Your Active Directory from Kerberoasting Attacks: A Practical Guide for IT Teams.
But before we go further, it’s important to understand what a password hash is.
What is a Password Hash?
A password hash is a fixed-length string generated by processing a plaintext password through a mathematical hashing algorithm. A strong hashing algorithm must adhere to these three key concepts:
- It must be one-way.
- It must be repeatable.
- Hash collisions must be extremely improbable.
These hashes are one-way functions, making it extremely difficult to reverse-engineer the original password. They are repeatable, meaning the same password will always generate the same hash with the same algorithm, and they avoid hash collisions, ensuring unique hashes for different inputs. Hashes are used in authentication systems to verify passwords without storing them in plaintext, thus enhancing security by avoiding the transmittal and storage of plaintext passwords.
How can an Attacker use a Password Hash?
If an attacker has the hashed value of a user’s password, they can authenticate on the network without needing to know anything about the plaintext password. This gives the attacker equivalent access as if they knew the user’s actual password, and applications and authentication mechanisms are none the wiser.
PtH attacks were first disclosed in 1997, a few years before the release of Windows 2000, when Kerberos replaced NTLM as the default authentication mechanism. While technologies have evolved significantly in the decades since, the PtH attack technique is still practical and prevalent.
Here’s an example: A coordinated attack in April 2022 targeted Microsoft Exchange Server deployments across companies in several sectors. Microsoft had patched a vulnerability known as ProxyShell in 2021, but unpatched Exchange servers provided a method for attackers to exploit the vulnerability and gain admin access to the Exchange server. Once they had admin access, they were able to use tools like Mimikatz to harvest password hashes of Domain Admin accounts which had logged in to the server and then start to move laterally in the network with full Domain Admin privileges.
Common Targets of Pass-the-Hash Attacks
NTLM Authentication
NTLM (New Technology Lan Manager) is the main authentication mechanism vulnerable to pass-the-hash attacks in Windows environments. NTLM also supports the older LM (Lan Manager) authentication for compatibility, though LM use is discouraged in modern environments.
In NTLM authentication, an application collects the user’s username and password, hashes the password, and sends a logon request to a domain controller. If the hash matches the one stored in the Active Directory database, the user is authenticated.
Most Active Directory systems prefer Kerberos over NTLM, but this requires proper configuration. If Kerberos is unavailable, NTLM acts as the fallback. Many applications still rely on NTLM, making it impractical to disable it entirely.
Administrative & Privileged Accounts
Attackers will target systems where they may be able to gather the hashes of administrative accounts. Like with the Microsoft Exchange Server ProxyShell vulnerability, any system where an administrator account is being used makes for a high-value target. It’s important to harden and monitor these systems—treat them as Tier 0 assets! —to detect and prevent possible PtH attacks. For more on what Tier 0 means, check out our blog post on the Tiered Access Model.
How a Pass-the-Hash Attack Works
A successful PtH attack involves two main steps:
- Harvest password hashes for local or domain accounts.
- Authenticate using the harvested hash on a matching user account.
Harvesting Password Hashes
Attackers can steal password hashes in various ways, but they typically need administrative access to a system. Vulnerabilities and malware can grant this level of access, which can be hard to detect without proper hardening and security monitoring. Phishing attacks can either provide access to an account or trick a user into installing malware that grants system access. Once an attacker has administrative access, they can use specialized tools to expose password hashes.
SAM Database
The SAM (Security Account Manager) database on a Windows system stores usernames, passwords, and group information for local accounts. And while it doesn’t store usernames and passwords for domain accounts, if an admin reuses a password from a local account on a domain account, then the password hash would work for both accounts.
LSASS Process
The LSASS (Local Security Authority Subsystem Service) process runs on all Windows systems and manages credentials and security policies. It stores hashes for any active logon sessions, including local and domain accounts from interactive and remote logins. Even remote access via RDP can result in the user’s password hash being stored in LSASS memory.
Tools
Many widely used tools can expose password hashes. Here are a few:
- Mimikatz: An open-source tool commonly used by penetration testers and security researchers, as well as bad actors. It allows for extraction of various authentication credentials in Windows and is easy to detect with security software.
- DaRT: The Microsoft Diagnostics and Recovery Toolset includes a tool called LockSmith and can reset any local account password.
- Cain & Abel: A Windows password recovery tool, like LockSmith.
- Windows Credential Editor (WCE): This open-source tool allows for direct modification of credentials for active sessions in Windows and for credential export. An attacker could use it to authenticate as one user and then change their credentials to impersonate another.
Authenticating Using a Stolen Password Hash
Once an attacker has a password hash, then can authenticate as the corresponding user. Fortunately, most applications do not accept a password hash in place of an actual password. However, attackers can use other methods to supply the password hash instead, utilizing tools like those mentioned in the previous section.
Detecting Pass-the-Hash Attacks
Detecting a PtH can be difficult. An attacker using a stolen password hash will often appear to be legitimate, however, there are still steps we can take.
1. Identify the signs of a PtH attack.
- PtH attacks will often show up as successful authentications from users on unusual devices or from unusual network locations.
2. Use AD-aware security tools like Microsoft Defender for Identity or Semperis DSP (Directory Services Protector).
3. Monitor Security Event 4624: An account was successfully logged on.
4. Use a continuous monitoring solution like a SIEM (Security Information and Event Management) system.
5. Use an IDS/IPS (Intrusion Detection/Prevention System).
- This can help detect unexpected transmission of password hashes from unusual locations.
6. Use an EDR (Endpoint Detection and Response) solution like Microsoft Defender for Endpoint to detect and prevent inappropriate access to password hashes on endpoints.
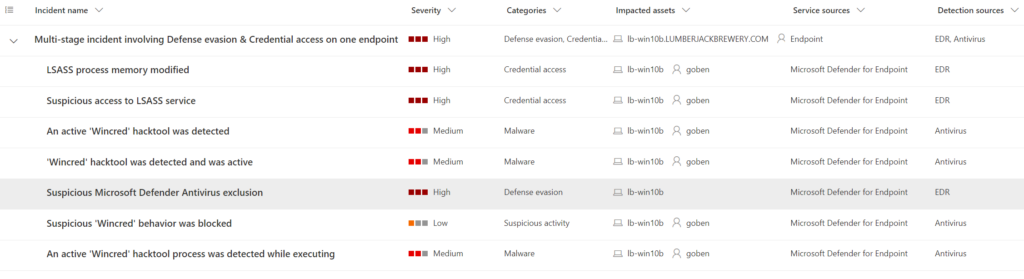
- For example, this screenshot shows alerts generated from a device running Microsoft Defender for Endpoint being attacked with the WCE tool. The attack was initially prevented, but a user with local admin rights can bypass protections to allow successful execution while still being detected and generating alerts.
Preventing Pass-the-Hash Attacks
Preventing the success of a PtH attack requires a combination of security best practices and defense-in-depth techniques, such as implementing a Zero Trust security model. Here are some methods to protect your environment from PtH attacks.
Implement a Tier-0 Administrative Environment
- Require the use of multifactor authentication for accessing Tier 0 systems. This can include the use of smartcards or FIDO2 authentication methods, like security keys or Windows Hello for Business.
- Limit administrative access whenever possible using the concept of JEA (Just Enough Administration). Users who need a limited amount of administrative access should only be granted the permissions they need rather than full admin access.
- Restrict local administrator rights to only approved IT personnel where possible.
- Ensure administrators are using secondary accounts for administrative tasks.
- Use a PAM and JIT (Privileged Access Management and Just in Time Administration) solution. This grants time-gated permissions for admin accounts only when elevated permissions are needed. For example, a Domain Admin account assigned to an engineer who is at home at 3 am does not need to be a member of the Domain Admins group while they are asleep.
- Require regular password changes for administrative accounts. This can be managed automatically by most PAM systems.
- Ensure passwords are not reused among admin or service accounts. If a local account password is reused on a domain account, then a compromise of the local account’s password hash compromises the domain account as well.
Harden and Monitor System and Network Security
- Use a local administrator password rotation solution, like Windows LAPS or CyberArk EPM. This will allow for the approved use of a local administrator account with automatic password rotation after the account is no longer being used.
- Implement network segmentation with modern firewalls.
- PtH attacks can be limited by only allowing access to certain systems from other known network locations and devices, like using PAWs (Privileged Access Workstations) to administer Tier 0 systems.
- Use an XDR system like Microsoft Defender to monitor identities, devices, and networks.
- Use an EDR system like Microsoft Defender for Endpoint on endpoints (workstations and servers).
- Configure and prefer Kerberos over NTLM whenever possible in your Active Directory environment. For more on how to prefer Kerberos, check out Should I Upgrade Active Directory Domain Services to Windows Server 2025?
- Ensure systems are patched regularly to stay up to date with current patch releases to limit attacker’s ability to use known vulnerabilities.
Use Modern Authentication Capabilities
- Require MFA whenever possible for all users.
- Even if an account is compromised in the Active Directory environment, cloud services can still require an additional MFA approval.
- Implement passwordless authentication, like Windows Hello for Business, FIDO2, or Smart Cards.
- Implement Microsoft’s Credential Guard and Remote Credential Guard.
- Credential Guard uses Virtualization-based Security (VBS) to isolate and protect NTLM password hashes, ensuring that only privileged system processes can access them.
- Remote Credential Guard is a mechanism that uses Kerberos and allows RDP connections to be created without sending credentials over the network.
- For more detail, check out these Microsoft Learn articles on Credential Guard and Remote Credential Guard.
Conclusion
A successful pass-the-hash attack can be difficult to detect, but there are many steps you can take to prevent it. Using a strong defense-in-depth strategy with a Zero Trust model can significantly reduce the likelihood of a successful PtH attack, and using AD-aware security tools can help identify possible PtH attempts. The most important steps to prevent PtH attacks are to understand the signs, monitor the right signals across your environment, and proactively secure your systems.
If you would like help in developing or refining your strategy for protecting your environment from PtH attacks, we would be happy to consult with you. We have extensive experience in designing and implementing defense-in-depth strategies with Zero Trust solutions.
If you would like more information on Kerberos, don’t forget to check out our article on Kerberos and some of its security issues. And for staying up to date on emerging security threats, keep an eye on Microsoft’s Security Insider or CISA’s Cybersecurity Alerts page.










