The workstation an administrator uses to perform privileged tasks such as managing Active Directory (AD) is a high-value target for a potential adversary. If an adversary can gain control of the administrator’s workstation, they can use that control to carry out credential theft attacks or hijack the administrator’s session to perform elevated tasks beneficial to the adversary. Privileged Access Workstations (PAWs) are designed to mitigate this risk by providing administrators with a “clean keyboard” that is protected from threats.
By providing administrators with a clean keyboard, privileged access workstations isolate privileged accounts from the risks of a compromised workstation. Controls to remove or mitigate the risks of compromise paths such as Internet access, phishing, local administrator access, and key loggers are integral to the PAW design. Isolation of control paths such as Group Policy and network access must also be critical components.
Clean Source Principle
The clean source principle is a crucial component of a privileged access workstation design. The clean source principle dictates that any security-related dependency of a system must be managed to the same level of assurance. Put another way, given three systems in Figure 1 called A, B, and C, if A controls B and B controls C, A also transitively controls C.
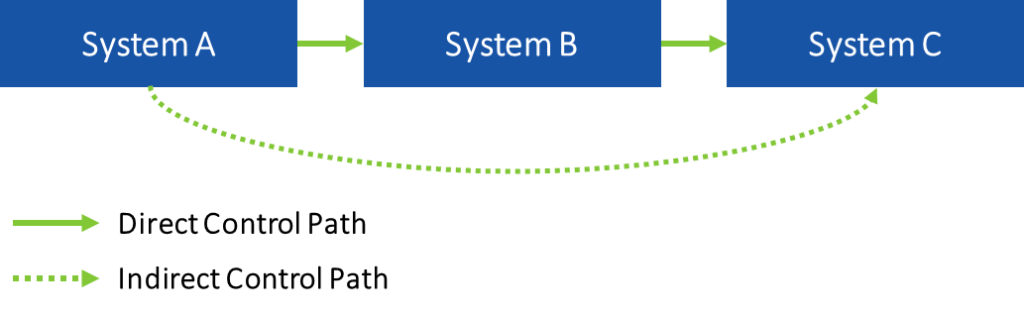
Figure 1 Control paths
This means that A must operate with the same security standards as B and C. In the AD tiering model, this is equivalent to ensuring that administrators in a lower tier (e.g., Tier 2) cannot exert control over a higher tier (e.g., Tier 1). Likewise, if System C is a member of Tier 0, System A and System B must also be members of Tier 0.
Although the example in Figure 1 is abstract, PAWs provide a very concrete example. The systems that control a given tier must not be dependent on or influenced by a system that is not also operated at the same level. For example:
- PAW hardware should be new-in-box to prevent potential compromise or tampering.
- The source media or image that provides the foundation for the PAW must be obtained directly from the vendor.
- If a PAW has unrestricted Internet access, for example, the clean source principle is clearly violated by the potential for an adversary to compromise the PAW by way of Internet browsing.
Your design and deployment model for PAWs must take the constraints of the clean source principle into account. Without this consideration, the security value of a PAW is substantially decreased.
Privileged Access Workstation Deployment Models
No matter how you deploy PAWs in your organization, there will be significant workflow changes for IT administrators. The deployment model you choose for your PAW implementation will play a major role in determining the workflow changes and long-term operational impact of the PAWs.
At Ravenswood, we utilize a few different PAW deployment models, depending on the customer’s needs and how many PAWs will be deployed. The simplest approach is to provide IT administrators with a second workstation (typically a laptop). While this is the least complicated model to deploy, it also means PAW users will need to take at least two laptops home with them or on the road when they travel. When you factor in test environments, privileged access forests, and PAW deployments extended into multiple AD tiers, the number of laptops necessary might grow quickly.
To mitigate this, we sometimes deploy a new PAW laptop that also runs a virtual machine (VM) containing the “productivity” image. In this model, IT administrators perform privileged tasks inside the base Windows installation on their workstation, but then they perform day-to-day computing tasks such as reading email and browsing the Internet inside a Hyper-V VM running on the laptop. This approach provides the isolation necessary to maintain the clean source principle with a PAW. Connecting to a virtual desktop infrastructure (VDI) instance from the PAW for day-to-day tasks is also a viable alternative. The opposite approach, however, is not viable. If the PAW is a VM on the laptop, VDI, or a jump server accessed from the IT administrator’s regular workstation, the clean source principle is broken.
The most complicated approach involves the use of shielded VMs on the PAW laptop. This brings significant assurance about the health and integrity of the host hardware, as well as isolation of multiple VMs running on the same laptop. The operational cost and complexity of shielded VMs is substantially higher than other deployment models, so you will need to weigh the benefits versus the cost.
Whichever model you choose, maintaining a clean keyboard in the PAW is the most important outcome. If you do not respect the clean source principle throughout the entire technology stack, you will dilute the value of the PAW and potentially even negate the security value altogether.
Issues to Consider
The technology stack used to deploy and manage your PAWs is a critical decision. To maintain the clean source principle, you will need to think about how you provision PAWs, network connectivity and virtual private networks (VPNs), identity and authentication, endpoint management, etc. In many cases the solutions you select for these areas must be separate from comparable solutions that are managing the rest of your client computers. At Ravenswood we often use a dedicated Microsoft 365 tenant with components such as Entra ID (formerly Azure Active Directory), Intune, and Microsoft Defender Advanced Threat Protection (ATP) to satisfy these requirements—but there are many different options and approaches available.
If you are planning a PAW implementation or looking to determine how best to begin hardening privileged access in your AD environment, our team can help. We work with large enterprises across the US and internationally to implement PAWs and establish broader AD hardening strategies. Please get in touch today if you would like to discuss how we can help your organization.













