First announced at WWDC in 2022, Platform SSO (PSSO) is now available for Microsoft Entra ID tenants. It can be configured on any supported macOS MDM, such as Microsoft Intune or Jamf, to allow users to sync local credentials with an identity provider. PSSO works remarkably well and deserves serious consideration.

Windows Hello for Business (WHfB) has strengthened and simplified user authentication and access management, enabling quick and secure SSO authentication to company resources. The ability to seamlessly use single sign-on (SSO) for cloud apps and on-premises resources has brought identity and device management into the modern era. PSSO introduces similar capabilities to any macOS device natively without the need for third-party software such as Jamf Connect or Nomad. Note that core PSSO functionality requires macOS 13+, but the most sought-after features are supported on only macOS 14+ devices.
Let’s explore how PSSO works, its various authentication methods, and how to implement it effectively on any Apple macOS device.
Authentication Methods
Partner with Microsoft experts you can trust
If it’s time to take that first step toward leveling up your organization’s security, get in touch with Ravenswood to start the conversation.
With the introduction of passkeys, authentication is becoming even more phish resistant. PSSO builds on enterprise SSO for macOS by incorporating its own hardware-bound passkey.
PSSO supports three authentication methods:
- Secure Enclave (platform credentials)
- Smart card
- Password
Secure Enclave provides the closest parity to WHfB on Windows, while the password method ensures the local password syncs with the Entra ID account. Smart cards include hard tokens such as YubiKey.
Please note, the password authentication method stores its keys in the iCloud Keychain, which users or attackers could export and reuse on a different device. Although such malicious events are limited, it is important to highlight because the security risk still exists.
Scenarios
There are several ways to configure Platform SSO depending on the requirements of the organization. Let’s review three potential scenarios.
A university has a computer lab with iMac devices that are shared amongst the student population. The university would like students to sign in with their Entra ID account.
Configure PSSO with an authentication method of password, ensuring the local password syncs with their Entra ID password. Enable user creation at login to allow students device access in the lab without administrative intervention.
A design studio has passwordless authentication deployed to all employees and is looking to deploy a fleet of MacBook M1 devices with PSSO.
Use Secure Enclave for PSSO and provide new hires with a Temporary Access Pass (TAP) to authenticate for the first time on their device. Employees can use Touch ID to authenticate cloud apps and company resources, fully supporting a passwordless environment.
A healthcare provider uses Mac mini devices around the facility, which various staff access to check patient reports. The organization would like to require smart cards for authentication to the internal systems.
Deploy a configuration profile to the Mac mini workstations with PSSO configured and set to smart card authentication. Enable user creation at login to support the shared-used environment and ensure a reader is available at each Mac device. Staff will now be prompted for smart card authentication when accessing any of the available workstations.
Platform SSO Walkthrough
Now we’ll go over the user experience of PSSO in action, including user registration and repairs.
A demo environment has deployed PSSO to its macOS fleet with the Secure Enclave authentication method. User creation at login has also been enabled. I was unable to capture a screen recording for the entire process, but let’s walk through a native cloud login.
A user, Jack Moore, signs into a MacBook. If Jack had previously signed in, he would be taken to the desktop or home screen. Otherwise, Jack will be guided through the Setup Assistant screen to customize the personalization settings, and then he will be sent to the home screen.
Logged in users can view their profile in System Preferences and review the PSSO configurations. Users can also repair a broken registration and reauthenticate tokens if needed.
If the PSSO configuration has changed the authentication method, all users will need to register again. In addition to the notification that appears periodically, users can visit this page to re-register.
All SSO users will have to register on a device configured with PSSO. If a user is not yet registered, they will periodically receive a notification requesting them to do so.
It is important for end users to enable Company Portal as a passkey provider. This allows the device-bound credentials to be used with SSO authentication.
Once Microsoft introduces support for authentication groups, tenant administrators can elevate certain groups to local administrators and others will remain as standard accounts.
With PSSO configured, signing into company resources is seamless. PSSO, which is implemented in the Microsoft Enterprise SSO extension, makes use of a broker (Company Portal). The logged in user automatically signs into any SSO-supported web application.
With Intune, tenant administrators can deploy the Microsoft SSO extension to applicable browsers such as Google Chrome. This enables support for SSO for the logged in user.
A Potential Gold-Standard Setup
PSSO offers a variety of customization settings that can be adjusted to best fit the organization. Although there are valid cases in which the password or smart card authentication methods can be used, the recommended approach is to use Secure Enclave. Let’s take a quick look at the most secure and optimal configuration currently available.
Choosing the Secure Enclave authentication method ensures phishing-resistant, passwordless authentication after device unlock. Microsoft and Apple both recommend using Secure Enclave due to its security in storing sensitive data such as tokens. A device-bound cryptographic key stored in Secure Enclave (similar to passkeys) authenticates resources like Microsoft Teams, Outlook, and third-party cloud apps configured with Microsoft Entra SSO.
Consider rolling out passwordless authentication to all SSO users and providing new hires with a TAP to authenticate for the first time, if necessary. If the user has already enrolled with the Microsoft Authenticator app for MFA, this is not necessary.
Deploying a device restriction to limit passwords to 6 or 8-digit passcodes brings parity with WHfB, creating a similar user experience to Windows. This approach separates cloud passwords from local passwords while maintaining optimal security. Users will configure Touch ID, replacing the need to use passcodes in most scenarios.
Enable user creation at login when signing in with an Entra ID account, which is especially useful for shared devices. If enabled, deploy a configuration profile to display username and password fields instead of the default login UI of selecting a user profile. Users can enter their Entra ID user principal name (UPN) and password to sign in for the first time on the device. They will then be routed through a quick Setup Assistant experience.
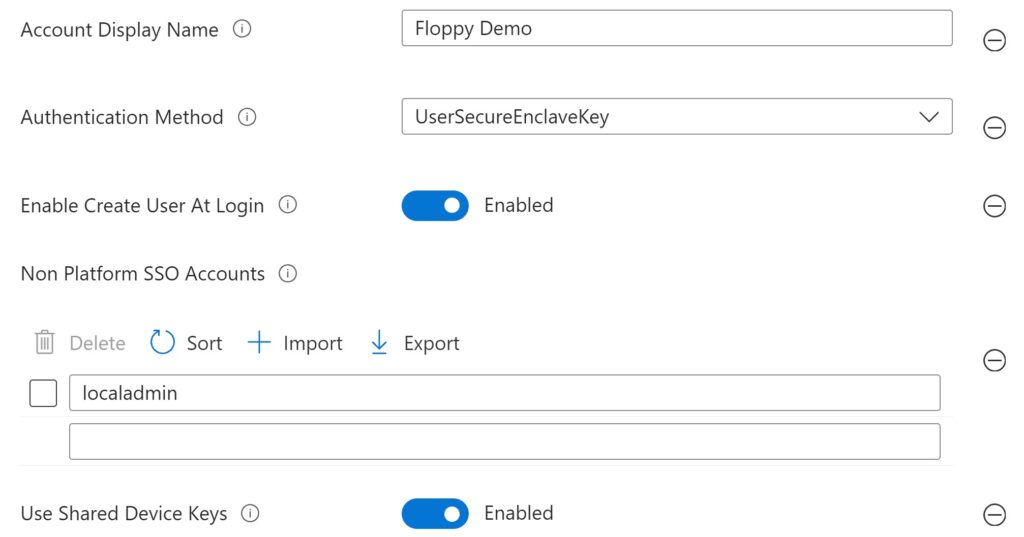
Regardless of how customized the PSSO configuration is, enable the “Use Shared Device Keys” setting shown in the screenshot below.
Changing this later will require re-registration for all users. Many features of PSSO, like “Enable Create User At Login,” require this setting to be enabled. If shared device keys are not used, PSSO will use per-user device keys, which limit the features available through PSSO. The main difference between the two types of keys is that the shared device keys allow for IdP authentication to occur at the lock screen, prior to the user signing into the device.
Conclusion
I hope this has been an informative showcase of PSSO and encourage testing this out in your own organization. As PSSO matures and features like authentication groups are implemented, user management will be very tailored to the needs of each organization. From user creation at login to syncing local passwords with Entra ID password, the future looks very bright for enterprise-managed macOS devices. If you’re interested in reading more about PSSO, the settings available, and what it takes to deploy it to your fleet, visit Microsoft’s documentation for details.
For help with Platform SSO, reach out to Ravenswood today! Our experts are here to help.













